
Executive Summary
In recent years, the global space sector has become an increasingly attractive target for nation-state actors seeking to gain strategic advantages. These actors often engage in cyber espionage to steal sensitive information and intellectual property, aiming to either disrupt space sector entities or enhance their own national space programs. Over the last year, several notable cyber espionage campaigns have specifically targeted space entities. Among these, recent reports have highlighted the activities of Andariel, a North Korean-linked hacking group, that has launched a global campaign against defense, aerospace, nuclear, and engineering organizations across the United States, Japan, South Korea, and India. This campaign is a stark reminder of the prevalence of state-sponsored cyber threats and their ongoing efforts to infiltrate space-related industries for espionage and intelligence collection.
Attack Pattern
Known for its sophisticated tactics and strategic objectives, Andariel has recently expanded its operations to include ransomware attacks against healthcare providers, energy companies, and financial institutions worldwide. Recognized for its formidable capabilities, Mandiant has since classified Andariel as an advanced persistent threat (APT45), emphasizing its sophistication and pervasiveness.
Andariel's operational history indicates a consistent focus on military and governmental personnel, aiming to gain access to sensitive information such as contracts, design drawings, bills of materials, and other critical engineering documents. Recent reports also indicate that Andariel has intensified its efforts to infiltrate aerospace entities, seeking to extract valuable intellectual property and technological insights that could enhance its state's defense and nuclear programs. According to assessments from federal agencies, this intelligence is leveraged to support North Korea's military and nuclear ambitions.
Andariel's attack methodology reflects a sophisticated understanding of modern cyber vulnerabilities. The group prioritizes the exploitation of web servers, often targeting known vulnerabilities in widely used applications. Notably, the group has capitalized on the infamous Log4j vulnerability, an Apache-based flaw that has been exploited globally since 2021. Andariel's proficiency in weaponizing vulnerabilities is evident in its array of exploits that target applications and devices commonly used in a variety of industries. Many of the targeted platforms have specific applications to space technology, from message brokers like Apache ActiveMQ, which can be used to handle communications between satellite networks, as well as devices that provide edge security and load balancing like Citrix Netscaler. The exploitation of these systems has been a key component of Andariel's initial access campaigns over the past two years, highlighting the group's technical prowess and adaptability.
Beyond exploiting technical vulnerabilities, Andariel employs a variety of social engineering techniques to infiltrate target networks. Phishing remains a central tactic, with the group distributing malicious attachments and .zip files to unsuspecting victims. These phishing campaigns are meticulously crafted to deceive users into executing malware, thereby granting Andariel access to sensitive systems and information.
Space Sector Targeting
Recent intelligence reports indicate that Andariel has shifted its focus towards the aerospace sector, engaging in cyber espionage campaigns designed to exfiltrate intellectual property related to satellite technology and communications. This strategic pivot aligns with North Korea's broader objectives to advance its technological capabilities and bolster its defense and nuclear programs.
Federal agencies, including the Cybersecurity and Infrastructure Security Agency (CISA), have documented Andariel's targeted attacks on aerospace entities, revealing the group's interest in satellite, satellite communications, and nano-satellite technology. In a recent advisory published by Microsoft Threat Intelligence on 25 July 2024, it was reported that Andariel, tracked under the alias "Onyx Sleet," deployed a Sliver implant—an open-source command-and-control (C2) framework—across multiple operators. This campaign, active from October 2023 to June 2024, successfully compromised several aerospace and defense sector entities, highlighting the group's capability to execute long-term, coordinated attacks on critical infrastructure.
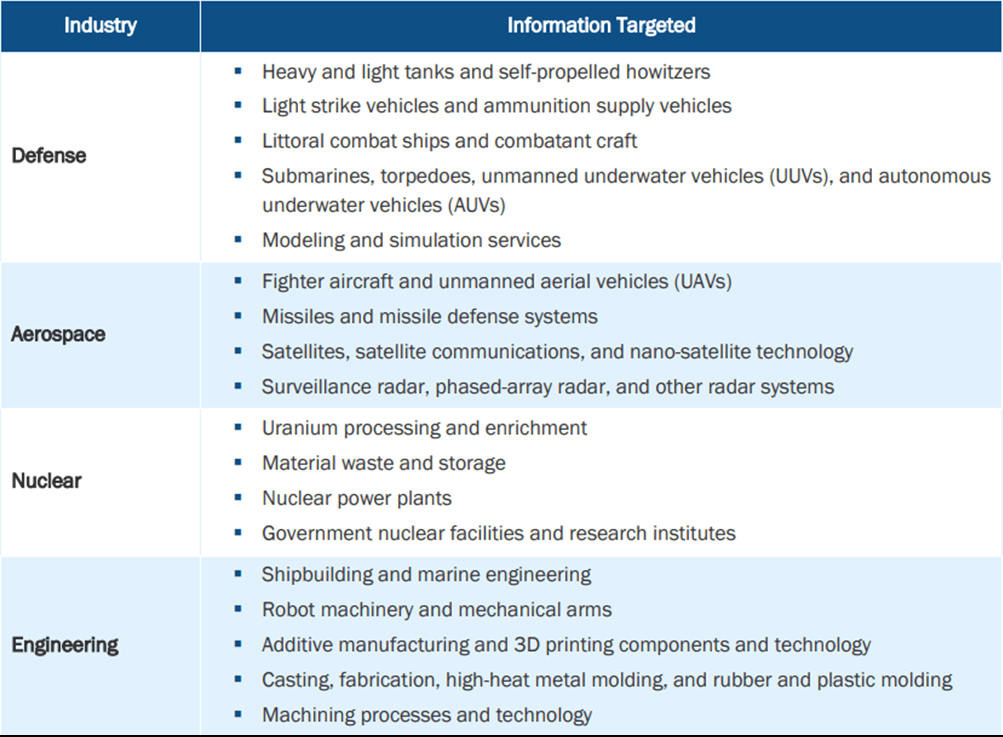 Table 1: Andariel Cyber Espionage Victimology
Table 1: Andariel Cyber Espionage Victimology
Ransomware Operations
Andariel's activities are not limited to espionage. The group has been actively involved in ransomware attacks, particularly targeting the U.S. healthcare sector. This approach is consistent with North Korean state-sponsored groups' broader strategy of using ransomware to circumvent U.S. sanctions and fund more advanced cybercriminal operations. By deploying ransomware payloads, Andariel effectively blurs the line between espionage and cybercrime, utilizing financial extortion as a means to support its strategic objectives. These ransomware operations serve dual purposes: generating revenue and creating a smokescreen for more covert espionage activities.
Conclusion
Andariel's recent campaigns against aerospace entities represent a significant escalation in its cyber operations, underscoring the evolving threat to commercial space. The group's ability to exploit technical vulnerabilities, coupled with its strategic focus on extracting sensitive information, reinforces the importance of robust cybersecurity measures and international cooperation to mitigate these types of sophisticated threats. Andariel’s activities are not isolated incidents but part of a broader pattern of state-sponsored campaigns aiming to extract valuable information and technology from space sector entities. As space continues to emerge as a crucial frontier for national security and economic growth, understanding and countering these cyber threats is imperative for maintaining global stability and protecting the integrity of space operations.
